TruffleHog is an open-source security scanner to detect secrets hidden in codebases. These secrets can include API keys, cloud provider credentials, passwords, and other sensitive tokens that, if exposed, may lead to serious security breaches. TruffleHog works by scanning through Git repositories, filesystems, or even entire commit histories to uncover potential leaks.
One of the challenges when using tools like TruffleHog is dealing with installation requirements, environment setup, and version mismatches across systems. By running TruffleHog inside a Docker container, you get a portable, isolated environment that works consistently across any Linux distribution.
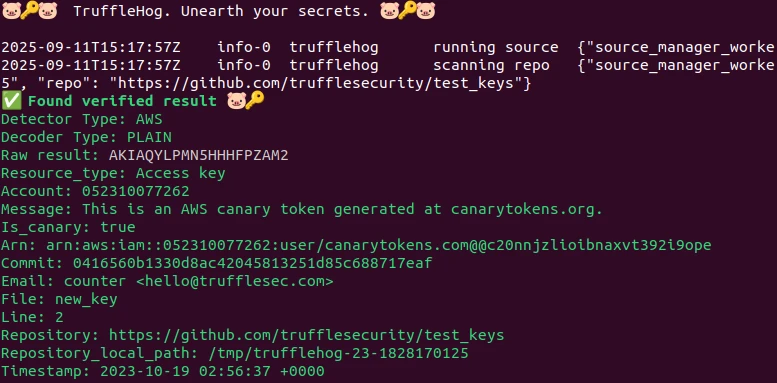
For example, if you want to scan a GitHub repository for exposed secrets using TruffleHog inside Docker, you can run the following command:
docker run -it --rm trufflesecurity/trufflehog git https://github.com/trufflesecurity/test_keys --results=verified,unknownExplanation of the command:
docker run- creates and launches a new container.-it- runs the container in interactive mode with a terminal.--rm- automatically removes the container after the scan completes, keeping the system clean.trufflesecurity/trufflehog- specifies the official Docker image for TruffleHog.git REPO_URL- tells TruffleHog to analyze the provided GitHub repository.--results=verified,unknown- configures the output to show both verified secrets (confirmed to be valid) and unknown ones (potential secrets that require manual review).
The command scans the specified repository and displays any detected results. Example output (truncated):




Leave a Comment
Cancel reply